Perimeter defencesNetwork protection
The boundaries between physical and digital continue to blur, and now all valuable information travels over interconnected networks. This is why companies need to review their network security models, equipping themselves with the right processes, technologies and resources to monitor and verify proper operation. At the same time, there is a need to develop a new approach to defending networks and endpoints, which are increasingly the focus of cyber criminals. Traditional tools can only provide certain security features and must be supplemented with innovative and effective solutions.


Mitigating vulnerabilitiesSecure and guaranteed accesses
It is not enough to study and develop passive countermeasures on the logical security level. You also need to implement solutions that help system administrators and end users use technology correctly to minimize cyber risks. Identifying vulnerabilities in the workplace is only the first step in addressing new threats: it is then essential to provide the corporate population with effective and easy-to-use tools to ensure secure access, even remotely, to the digital workplace.
A multilevel approachDefending cybersecurity according to WIIT
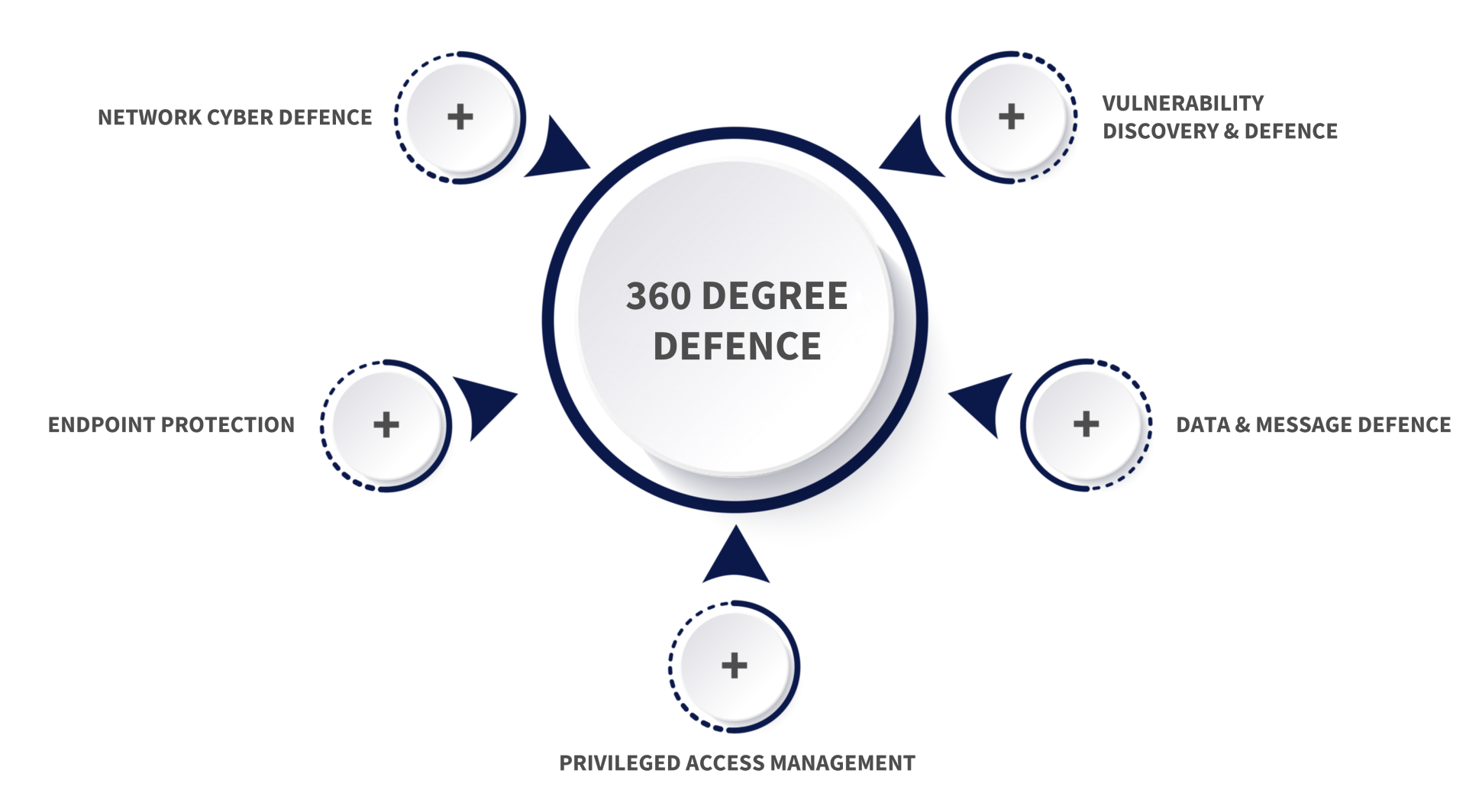
An integrated ecosystemDefending yourself 360 degrees
WIIT has created an integrated ecosystem of solutions and competencies for Cyber Security Defense that responds directly and concretely to all the needs of companies that have decided to focus on digital business innovation. From the classic Network Cyber Defense to Endpoint Protection, passing through the tools of Privileged Access Management and Vulnerability Discovery & Defense, up to Data & Message Defense, each organization today can customize its Cyber Defense solutions and protect its data and the services provided to clients 360 degrees.

360-degree defense

Network Cyber Defence
When we talk about Network Cyber Defence, reference is now made to a number of established solutions and technologies. The contribution of the cloud in the offer elaborated by WIIT transforms the classic Firewalling and Intrusion Detection and Prevention System tools into fundamental elements for up-to-date network security.
Endpoint Protection
Going beyond the logic of the traditional antivirus signature comparator, WIIT offers Endpoint Detection & Response solutions, which leverage advanced Threat Intelligence tools to analyze threats, provide risk indicators on user behaviour, and make real-time decisions.


Privileged Access Management
By creating a layer that manages access to IT systems and networks (target) through a single controlled point, the system administrator never comes into direct contact with the target but only with the Privileged Access Management solution, which takes care of performing the actions requested by the user in a secure and tracked manner.
Vulnerability Discovery & Defence
Vulnerability Management: a series of advanced tools able to systematically identify the vulnerabilities of the systems and report them in a contextual way to the technicians who can, consequently, implement remediation actions. The solution is provided as-a-Service by WIIT experts.


Data & Message Defence
Leveraging Threat Intelligence, email security solutions provide clients with advanced tools that can analyze messages through Threat Intelligence and Sandboxing technologies to detect cryptolocker, ransomware and phishing threats, as well as suspicious sources of various kinds.
The WIIT security index
Plant & Industrial Cyber Security tool management activities are also grafted onto the WIIT Security Index, which includes:
178Variables analyzed
5levels of depth
25weighted coefficients
100points overall points
5subscore per category
Vertical competencies for specific needs
The competence centers made available by WIIT are teams that the group has developed over the years through the implementation of projects in sectors with certified professionalism:



























